Be a loving person rather than in a love relationship because relationships happen one day and disappear another day. They are flowers; in the morning they bloom, by the evening they are gone. But people find it very difficult to be a loving person, a loving soul, so they create a relationship and be fool that way that "Now I am a loving person because I am in a relationship". And the relationship may be just one of monopoly, possessiveness and exclusiveness. The relationship is needed only because love is not there. Relationship is a substitute. Become alert! Relationship destroys love, destroys the very possibility of its birth.
Friday, 28 February 2014
On 22:59 by Unknown in algorithms, cipher protocol, cryptographic, data security, Lesson, security protocol, SSL, Tutorial No comments
Hello there, Welcome to our blog. How you all are, Hope you
all doing great. On our blog you will find support for tech, hacking and social
tweaks. We provide networking solutions for any type of problem. You can
contact us through this blog. We will do whatever we can do for your problem.
Have you checked our last tutorial About How DHCP works or how to configure DHCP on Packet Tracer.
Secure Socket Layer (SSL) is a security protocol that was developed by Netscape Communications Corporation, along with RSA Data Security, Inc. The Primary goal of the SSL protocol is to provide a private channel between communicating applications, which ensures privacy of data, authentication of the partners, and integrity. The Secure Socket Layer (SSL) technology was used for the websites or web applications which need more security.
Secure Socket Layer (SSL) is composed of two layers:
- At the lower layer, a protocol for transferring data using a variety of predefined cipher and authentication combinations, called the SSL Record Protocol.
- On the upper layer, a protocol for initial authentication and transfer of encryption keys, called the SSL Handshake Protocol.
An SSL session is initiated as follows:
- On the client (browser), the user requests a document with a special URL that starts with https: instead of http: either by typing it into the URL input field, or by clicking the link. For example the major search engines like Google, Yahoo, Bing and other money transactions websites uses Secure Socket Layer (SSL).The client computers which do not installed the Secure Socket Layer (SSL) certificates on their computer unable to browse those sites.
- The client code recognizes the SSL request and establishes a connection through TCP port 443 to the SSL code on the server.
- The client then initiates the SSL handshake phase, using the SSL Record Protocol as a carrier. At this point, there is no encryption or integrity checking built into the connection.
The Secure Socket Layer (SSL) Protocol addresses the following security issues:
- Privacy: After the symmetric key is established in the initial handshake, the messages are encrypted using this key.
- Integrity: Messages contain a message authentication code (MAC) ensuring the message integrity.
- Authentication: During the handshake, the client authenticates the server using an asymmetric or public key. It can also be based on certificates. SSL requires that each message is encrypted and decrypted and therefore has a high performance and resource cost.
Secure Socket Layer (SSL) Protocol
The SSL protocol is located at the top of the transport layer. SSL is also a layered protocol itself. It simply takes the data from the application layer, re-formats it, and transmits it to the transport layer. SSL handles a message as follows.
The sender performs the following tasks
- Takes the message from upper layer.
- Fragments the data to manageable blocks.
- Optionally compress the data.
- Applies a message authentication code (MAC)
- Encrypts the data.
- Transmits the result to the lower layer.
The receiver performs the following tasks.
- Takes the data from lower layer.
- Decrypts.
- Verifies the data with the negotiated MAC key.
- Decompress the data if compression was used.
- Reassembles the message.
- Transmits the message to the upper layer.
An SSL session works in different states. These states are session and connection states. The SSL handshake protocol coordinates the states of the client and the server. In addition, there are read and write states defined to coordinate the encryption according to the change Cipher Spec messages.
Change Cipher Spec Protocol
The change Cipher Spec protocol is responsible for sending change Cipher Spec messages. At any time, the client can request to change current cryptographic parameters such as the handshake key exchange. Following the change Cipher Spec notification, the client sends a handshake key exchange and if available, certificate verify messages, and the server sends a change Cipher Spec message after processing the key exchange message. After that, the newly agreed keys will be used until the next change Cipher Spec request. The change Cipher Spec message is sent after the hello messages during the negotiation.
SSL handshake protocol
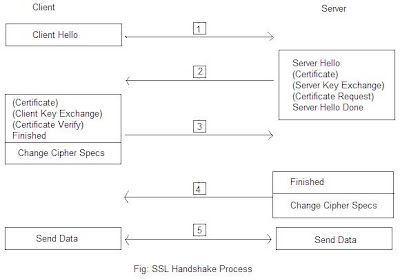
The SSL handshake protocol allows the client and server to determine the required parameters for and SSL connection such as protocol version, cryptographic algorithms, optional client or server authentication, and public key encryption methods to generate shared secrets. During this process, all handshake messages are forwarded to the SSL record layer to be encapsulated into special SSL messages. Figure below illustrates an SSL handshake process.
SSL record protocol
After the master key has been determined, the client and server can use it to encrypt application data. The SSL record protocol specifies a format for these messages in general, they include a message digest ensure that they have not been altered and the whole message is encrypted using a symmetric cipher.
Subscribe to:
Post Comments (Atom)
Search
Popular Posts
-
Hello there, Welcome to our blog. How you all are, Hope you all doing great. On our blog you will find support for tech, hacking and so...
-
OPEN MS-DOS Source Code Early tech fans might remember the good 'ol days of Microsoft MS-DOS, the company's first operating s...
-
Hello folks, How are you all. Today I'm here to bring you on of the most amazing hacking news or trick you can say. So let's begin ...
-
Hello, there again some poetry. This time i wrote this for someone who is close to my heart. Not close indeed very much close to me. I...
-
Hello there, Welcome to our blog. How you all are, Hope you all doing great. On our blog you will find support for tech, hacking and soc...
-
Google has begun a Glass at Work initiative, asking businesses how they're working with Glass, and the kinds of applications they...
-
Hello folks, this is my first post. M gonna explain about Pat and will give configuration for it with an example below. Port Address...
-
Hello there, Welcome to our blog. How you all are, Hope you all doing great. On our blog you will find support for tech, hacking and soc...
-
Hello there, Do you know when you submit a page on stumble upon then what happen. Under which process it goes?. Um, No. Oh, You need not t...
Categories
ACL
APPS AND SOFTWARE
Account Hacking
Adobe Flash Player
Android
BREAKING NEWS
Basic Networking
Bluetooth Hacking
Bus Tupology
CCNA
CCNA Security
CCNA1
CCNA2
CCNA3
CCNA4
Cloud Storage
Credit Card Hacking
Cyber Criminal
Cyber security
DEVELOPERS
Encrypted Password
Encryption
FTP
FTP Server
GOOGLE GLASS
Google Hacking
Mark Zuckerberg
Media Hacked
NASA
Network Hacking
Port security
Programming
SOCIAL MEDIA
SOCIAL NETWORKS
algorithms
ccna discovery
ccna exploration
facebook
hacking tool
internet and network security
packet tracer tutorial
Blog Archive
Get Content For Your Website
Get a 150-300 word article written for : $1.50
Get a 700-1000+ word article written for : $5.00
Have a 150-300 word article rewritten for : $1.25
Have a 700-1000+ word article rewritten for : $4.25
Get a 700-1000+ word article written for : $5.00
Have a 150-300 word article rewritten for : $1.25
Have a 700-1000+ word article rewritten for : $4.25




0 comments:
Post a Comment