Be a loving person rather than in a love relationship because relationships happen one day and disappear another day. They are flowers; in the morning they bloom, by the evening they are gone. But people find it very difficult to be a loving person, a loving soul, so they create a relationship and be fool that way that "Now I am a loving person because I am in a relationship". And the relationship may be just one of monopoly, possessiveness and exclusiveness. The relationship is needed only because love is not there. Relationship is a substitute. Become alert! Relationship destroys love, destroys the very possibility of its birth.
Sunday, 16 February 2014
On 09:18 by Unknown in News, Security News, Technology News, Usa Hacker News, Vulnerability No comments
Hello there. Here comes one amazing thing that you must know. Yes, now anyone can track your phone with just a small, cheap set up. That's the hackers way i am talking about, how they peoples phone. want to know then read it along till the end.
Cellular phones have become a ubiquitous means of communications with over 5 billion users worldwide in2010, of which 80% are GSM subscribers. Due to theiruse of the wireless medium and their mobile nature, thosephones listen to broadcast communications that could reveal their physical location to a passive adversary.
University of Minnesota researchers found a flaw in AT&T and T-Mobile cell towers that reveals the location of phone users. The attack, described in a Research paper (Click to Download Pdf), is most useful for determining whether a target is within a given geographic area as large as about 100 square kms or as small as one square kilometer. It can also be used to pinpoint a target's location but only when the attacker already knows the city, or part of a city, the person is in.
Ph.D. student Denis Foo Kune says, “Cell phone towers have to track cell phone subscribers to provide service efficiently. For example, an incoming voice call requires the network to locate that device so it can allocate the appropriate resources to handle the call. Your cell phone network has to at least loosely track your phone within large regions in order to make it easy to find it“.
The messages contain I.D. codes. In order to match the codes to the cell phone number, researchers called the phone three times. The code that appeared three times in the same time period in which researchers were listening in is most likely the code of the cell phone.“From there we can use that I.D. to determine if you’re around a certain area or if you’re on a particular cell tower,” he said.
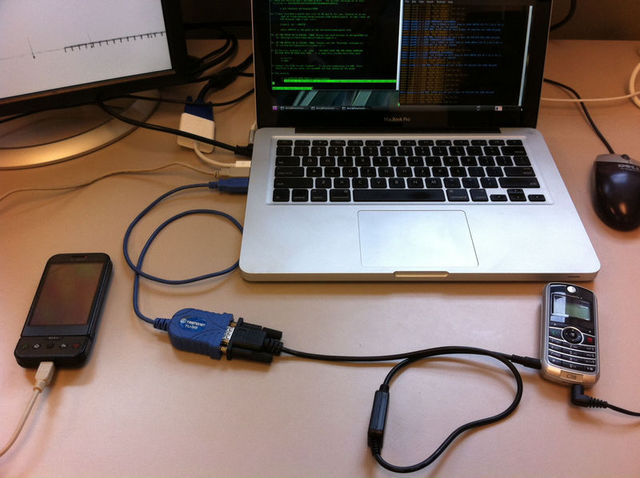
The process requires a feature cellphone and a laptop, running the open-source Osmocom GSM firmware and software respectively, along with a cable connecting the two devices. It also uses a separate cellphone and landline.
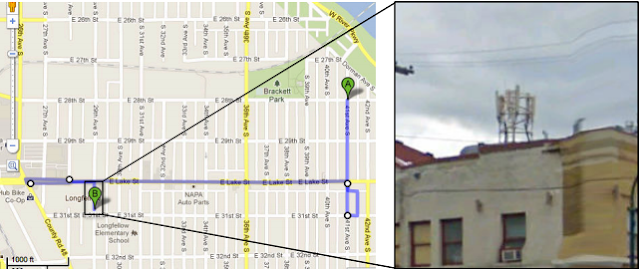
The attackers use the landline to call the target's cellphone when it's located near the same LAC as the equipment and use the laptop output to monitor the broadcasts that immediately follow over the airwaves to page the target phone.
The attackers use the landline to call the target's cellphone when it's located near the same LAC as the equipment and use the laptop output to monitor the broadcasts that immediately follow over the airwaves to page the target phone.
The implications of this research highlight possible personal safety issues. The group explains their work in a recently presented at the 19th Annual Network & Distributed System Security Symposium and was titled “Location Leaks on the GSM Air Interface”. The group has also contacted AT&T and Nokia with some low-cost options that could be implemented without changing the hardware.
Subscribe to:
Post Comments (Atom)
Search
Popular Posts
-
OPEN MS-DOS Source Code Early tech fans might remember the good 'ol days of Microsoft MS-DOS, the company's first operating s...
-
Hello there, Welcome to our blog. How you all are, Hope you all doing great. On our blog you will find support for tech, hacking and so...
-
Hello folks, How are you all. Today I'm here to bring you on of the most amazing hacking news or trick you can say. So let's begin ...
-
Hello, there again some poetry. This time i wrote this for someone who is close to my heart. Not close indeed very much close to me. I...
-
Hello there, Welcome to our blog. How you all are, Hope you all doing great. On our blog you will find support for tech, hacking and soc...
-
Hello folks, this is my first post. M gonna explain about Pat and will give configuration for it with an example below. Port Address...
-
Hello there, Welcome to our blog. How you all are, Hope you all doing great. On our blog you will find support for tech, hacking and soc...
-
Google has begun a Glass at Work initiative, asking businesses how they're working with Glass, and the kinds of applications they...
-
Hello there, Do you know when you submit a page on stumble upon then what happen. Under which process it goes?. Um, No. Oh, You need not t...
Categories
ACL
APPS AND SOFTWARE
Account Hacking
Adobe Flash Player
Android
BREAKING NEWS
Basic Networking
Bluetooth Hacking
Bus Tupology
CCNA
CCNA Security
CCNA1
CCNA2
CCNA3
CCNA4
Cloud Storage
Credit Card Hacking
Cyber Criminal
Cyber security
DEVELOPERS
Encrypted Password
Encryption
FTP
FTP Server
GOOGLE GLASS
Google Hacking
Mark Zuckerberg
Media Hacked
NASA
Network Hacking
Port security
Programming
SOCIAL MEDIA
SOCIAL NETWORKS
algorithms
ccna discovery
ccna exploration
facebook
hacking tool
internet and network security
packet tracer tutorial
Blog Archive
Get Content For Your Website
Get a 150-300 word article written for : $1.50
Get a 700-1000+ word article written for : $5.00
Have a 150-300 word article rewritten for : $1.25
Have a 700-1000+ word article rewritten for : $4.25
Get a 700-1000+ word article written for : $5.00
Have a 150-300 word article rewritten for : $1.25
Have a 700-1000+ word article rewritten for : $4.25




0 comments:
Post a Comment